Signing Workflows
Explore different code signing workflows supported by QCecuring.
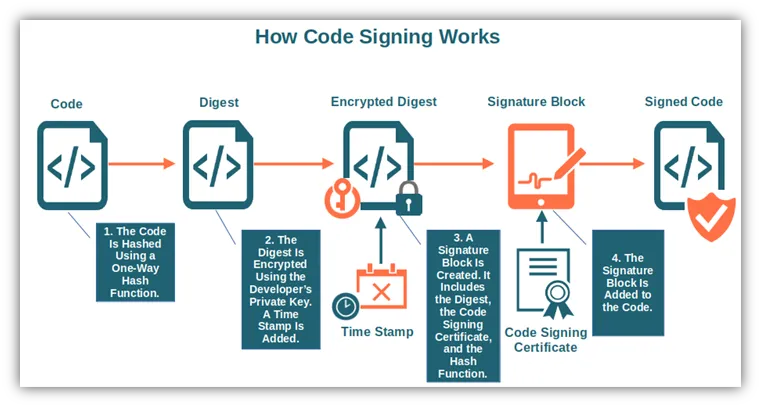
Digest-Based Signing
Section titled “Digest-Based Signing”Digest-based signing is the recommended and most secure workflow. Clients compute a cryptographic hash (digest) locally and submit only the digest to the signing API. The platform signs the digest using HSM-protected keys and returns the signature for local attachment to the artifact.
Why use it:
Section titled “Why use it:”- Minimizes transfer of sensitive or large artifacts
- Works with large binaries and CI/CD pipelines
- Keeps private keys inside HSM/KMS boundaries
Basic Steps
Section titled “Basic Steps”- Compute digest locally (SHA-256 example):
openssl dgst -sha256 -binary myapp.exe > digest.binbase64 digest.bin > digest.txt- Submit digest to the API:
curl -X POST https://api.example.com/api/v1/sign/digest \ -H "Authorization: Bearer $TOKEN" \ -H "Content-Type: application/json" \ -d '{"digest":"<base64-digest>", "algorithm":"sha256", "metadata": {"filename":"myapp.exe"}}'-
Platform signs the digest using HSM and returns a signature (and optional RFC 3161 timestamp token).
-
Attach signature to the artifact using platform-specific tools (jarsigner/signtool) or bundle the signature with metadata.
Best Practices
Section titled “Best Practices”- Always use binary digest (not hex string) and a well-defined encoding (base64 recommended).
- Verify signature locally after receiving it to ensure correct algorithm and chain.
- Use timestamping to preserve signature validity beyond certificate expiry.
Asynchronous Signing
Section titled “Asynchronous Signing”For high-volume or non-blocking pipelines, use asynchronous signing. The API accepts the digest request and returns immediately with a request identifier; workers process the job in the background and update status when completed.
- Client POSTs digest → API responds with
202 Acceptedand{ "requestId": "abc123" }. - Worker services dequeue jobs and call HSM to sign digests.
- Client polls
/api/v1/sign/requests/{requestId}to obtain final status (QUEUED,PROCESSING,SIGNED,FAILED).
Example request:
curl -X POST https://api.example.com/api/v1/sign/digest -H "Authorization: Bearer $TOKEN" -d '{"digest":"<base64>","async":true}'# Response: {"requestId":"abc123"}
# Pollcurl https://api.example.com/api/v1/sign/requests/abc123 -H "Authorization: Bearer $TOKEN"# Response: {"status":"SIGNED","signature":"...","timestamp":"..."}Operational notes
Section titled “Operational notes”- Monitor queue depth and worker latency; scale workers based on queue metrics.
- Use dead-letter queues for persistent failures and implement idempotency tokens to avoid double processing.
Quorum Approvals
Section titled “Quorum Approvals”Quorum approvals add human oversight to sensitive signing operations. Policies can require N approvals from an approver group before the request is signed.
- Client submits digest marked as requiring approval.
- Platform marks request
PENDING_APPROVALand notifies approvers. - Approvers review metadata and approve/reject via the portal or API.
- Once threshold reached, the request is queued for signing and processed by workers.
Example approver API
Section titled “Example approver API”POST /api/v1/approvals/{id}/approve— Approve a pending requestGET /api/v1/approvals/{id}— View approval status
Best practices
Section titled “Best practices”- Define approver groups with clear separation of duties.
- Keep audit trails for approvals and require justification/comments for sensitive approvals.