Architecture Overview
Architecture Overview
Section titled “Architecture Overview”Short Summary: SSL-CLM uses a hub-and-spoke architecture where a central Control Plane (Backend) manages distributed execution nodes (Agents) and connects to upstream authorities (Gateways).
Component Diagram
Section titled “Component Diagram”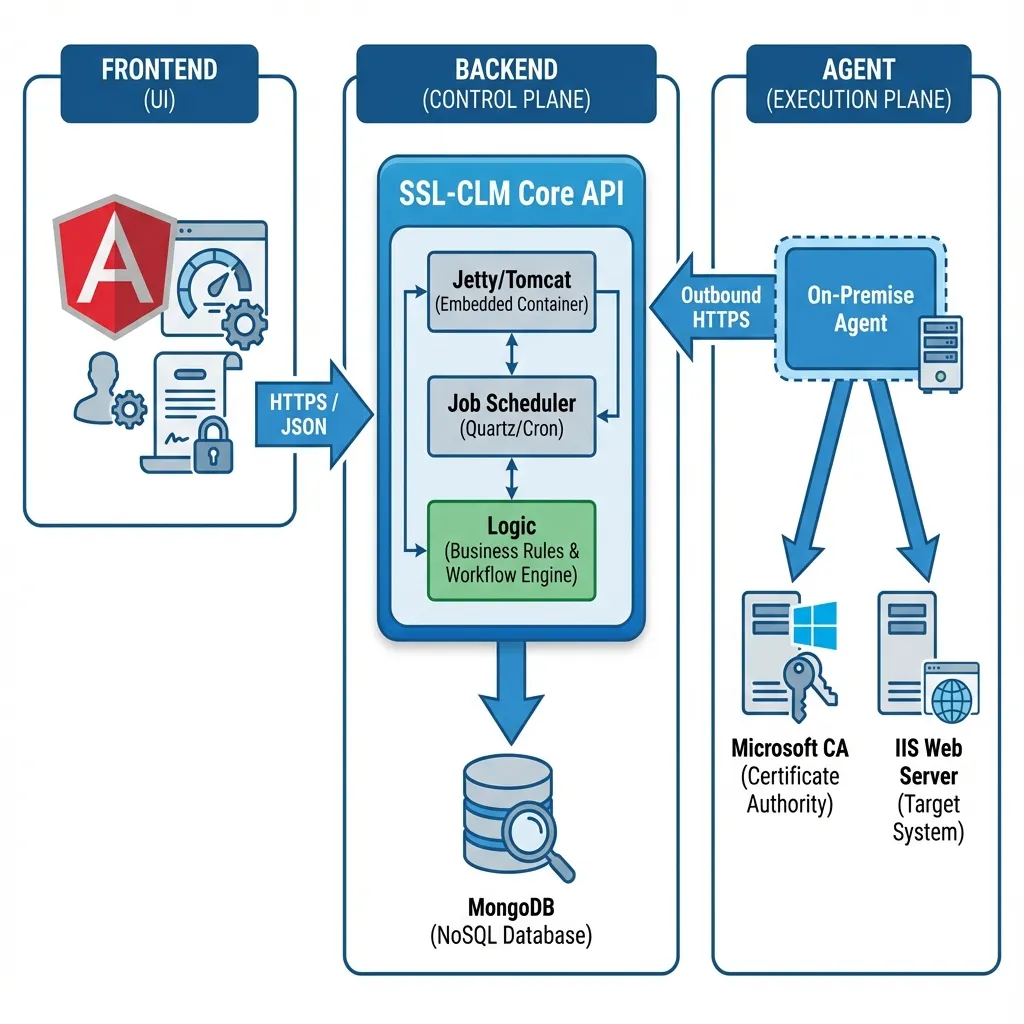
Core Components
Section titled “Core Components”1. Control Plane (Backend)
Section titled “1. Control Plane (Backend)”The central “brain” of the system.
- API Layer: REST/JSON API for all interactions.
- Job Scheduler: Quartz-based engine for scheduling scans and renewals.
- Policy Engine: Enforces cryptographic standards (e.g., “No SHA-1”).
- Inventory Database: MongoDB cluster storing the canonical state of all certificates.
2. Execution Plane (Agents)
Section titled “2. Execution Plane (Agents)”Lightweight binaries installed on target networks.
- Connectivity: Outbound-only (HTTPS) to the Backend. No inbound ports required.
- Capabilities:
- Network Scanning: Discover certificates on local subnets.
- Local Management: Generate keys and install certificates on IIS, Apache, etc.
- MSCA Bridge: Communicate with internal Microsoft CAs via DCOM.
3. Integration Layer (Gateways & Connectors)
Section titled “3. Integration Layer (Gateways & Connectors)”Plugins that adapt SSL-CLM to external systems.
- CA Gateways: DigiCert, Let’s Encrypt (ACME), AWS Private CA.
- Store Connectors: AWS ACM, Azure Key Vault, F5 BIG-IP.
Data Flow: Usage vs. Management
Section titled “Data Flow: Usage vs. Management”- Management Plane: SSL-CLM (Traffic: Job instructions, Metadata, CSRs).
- Data Plane: Your Web Servers (Traffic: Actual HTTPS traffic).
Note: SSL-CLM is out-of-band. If SSL-CLM goes down, your existing certificates continue to work, and your web traffic is unaffected.