Renewal Lifecycle
Renewal Lifecycle
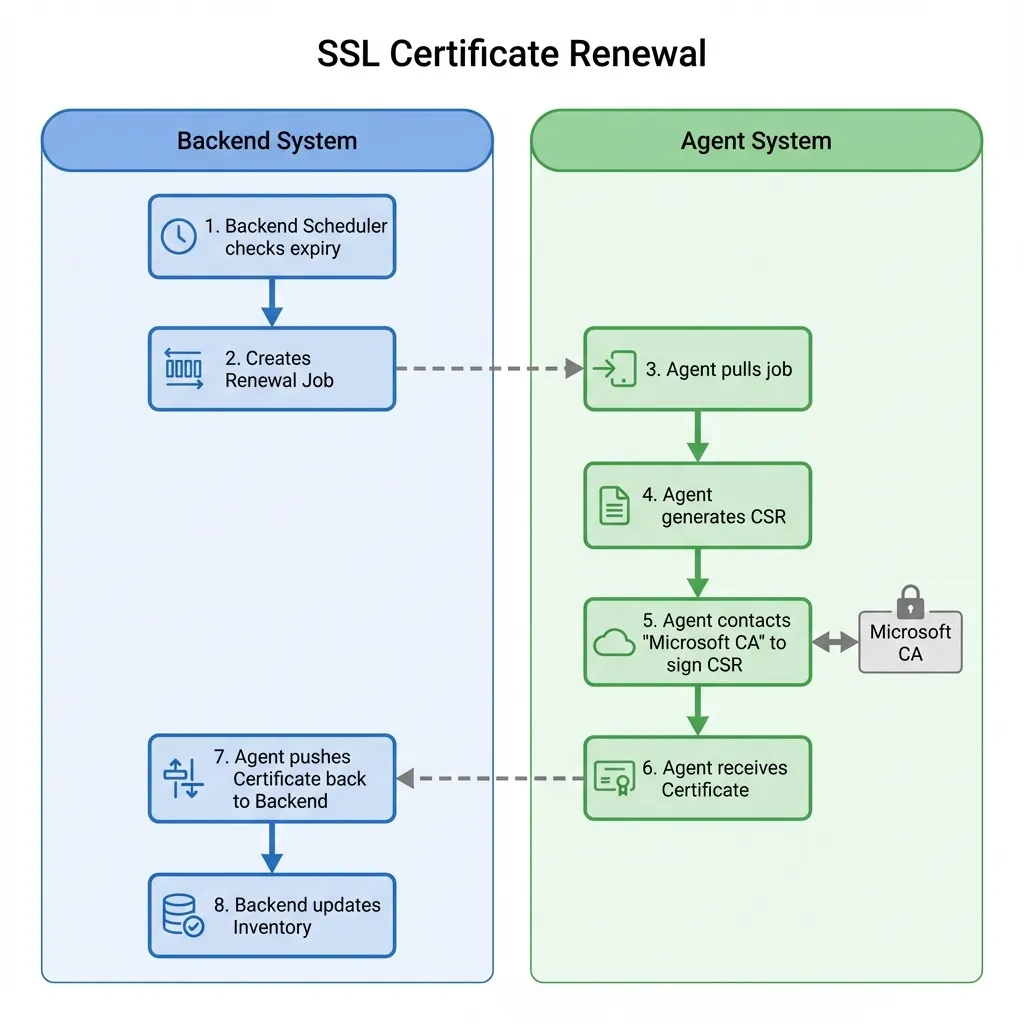
Section titled “Renewal Lifecycle”Short Summary: The Renewal Lifecycle is the core automation workflow of SSL-CLM, ensuring certificates never expire unexpectedly.
The State Machine
Section titled “The State Machine”A certificate moves through specific states during renewal:
- Monitor: Certificate is healthy. Scheduler checks expiry daily.
- Renewal Window: Certificate enters the “Renewal Window” (default: 30 days before expiry).
- Job Created: A
RENEW_CERTjob is queued. - Processing:
- CSR Generation: Agent generates a new Key Pair and CSR.
- Submission: CSR sent to CA.
- Validation: CA validates domain (e.g., ACME challenge).
- Issuance: CA signs and returns the CRT.
- Installation: Agent binds the CRT to the web server.
- Complete: Inventory updated with new expiry date.
Renewal Strategies
Section titled “Renewal Strategies”1. New Key (Re-Key) - Recommended
Section titled “1. New Key (Re-Key) - Recommended”- Process: A brand new Private Key is generated.
- Security: High. Limits the impact of potential key compromise.
2. Reuse Key
Section titled “2. Reuse Key”- Process: The existing CSR/Key is resubmitted.
- Use Case: Legacy systems where key updates are difficult (Pinning).
- Note: Not supported by all CAs.
Policy Guardrails
Section titled “Policy Guardrails”Renewal is governed by Policies.
- Auto-Approve: Can this certificate renew automatically?
- Approval Required: Does a manager need to click “Approve” first (e.g., for EV certs)?
Diagram
Section titled “Diagram”